Friday, March 16. 2012
Principled Technologies Report - View 5 Compared to Citrix XenDesktop 5.5
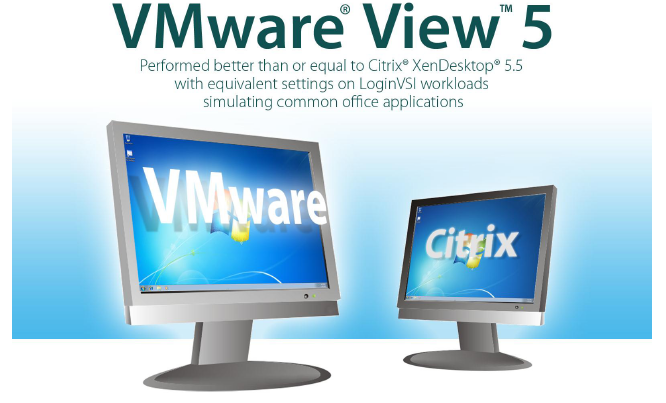
This report shows that in a true apples-to-apples comparison where lossy and lossless policies are applied equally to both platforms to yield a comparable user experience, VMware View 5 demonstrates equal or better efficiency in bandwidth consumption and in client and server side CPU utilization when compared to Citrix XenDesktop 5.5 on common office applications. This advantage in efficiency can translate into great density, better user experience and lower cost for an organization using VDI technologies.


Thursday, March 15. 2012
VMware has released version 1.4 of their View Client for iPad
- Improved connection times to View server
- Improved support for external monitors
- Bug fixes
Wednesday, March 14. 2012
VMware View 5 - Technical Papers
The Business Case for Desktop Virtualization
In this mobile user- and device-centric environment, IT must protect data security and control user access to data at the same time as it manages the range of applications and devices for all users. The single operating system and single device per user is a model of the past. VMware offers an end user computing solution that meets the challenges of providing for a mobile workforce, without compromising IT control or the operational efficiencies of existing management processes. VMware products incorporate the needs of both IT and end users.
Secure Printing with VMware View
Security Solution Architecture for VDI
This brief provides an overview of the desktop security vulnerabilities which exist in both virtual and physical environments that must be addressed throughout the typical connection sequence, along with the VMware and thirdparty products that remediate the issues. Together, VMware and VMware technologies comprise a security solution architecture for virtual desktop infrastructure (VDI)—an architecture that goes beyond the viruses, worms, and phishing attacks mostly commonly addressed in desktop security technology to include data loss, system management, and compliance monitoring.
Antivirus Practices for VMware View 5
In this mobile user- and device-centric environment, IT must protect data security and control user access to data at the same time as it manages the range of applications and devices for all users. The single operating system and single device per user is a model of the past. VMware offers an end user computing solution that meets the challenges of providing for a mobile workforce, without compromising IT control or the operational efficiencies of existing management processes. VMware products incorporate the needs of both IT and end users.
Secure Printing with VMware View
The first step in implementing Secure Print Release is to acquire the Secure Print Server solution from a printing partner. The Secure Print Control software will be installed on the same machine as your existing Print Server. The Secure Print Control software can use Active Directory for authentication or will integrate with an existing single sign-on solution. The Secure Print Control vendor solutions have modular SSO architecture and can work with you to integrate any existing SSO solution in your current infrastructure. Companies that do not want to use Active Directory or that have an existing SSO solution can alternatively use local lists or user input to a SQL database. The single sign-on and user login data are aggregated for compliance auditing purposes.
Security Solution Architecture for VDI
This brief provides an overview of the desktop security vulnerabilities which exist in both virtual and physical environments that must be addressed throughout the typical connection sequence, along with the VMware and thirdparty products that remediate the issues. Together, VMware and VMware technologies comprise a security solution architecture for virtual desktop infrastructure (VDI)—an architecture that goes beyond the viruses, worms, and phishing attacks mostly commonly addressed in desktop security technology to include data loss, system management, and compliance monitoring.
Antivirus Practices for VMware View 5
This paper focuses on the best practices for protection against viruses in the VMware View 5 virtual desktop environment. Antivirus software is one of the largest segments in today’s computer security market. Nearly every enterprise deploys antivirus software on every desktop. As services such as security, mobility, access control, and line-of-business applications are all rolled up into the datacenter or cloud, antivirus practices need to be rolled up as well.
Tuesday, March 13. 2012
VMware Workstation and Fusion Technology Preview 2012
The Technology Previews 2012 of VMware Workstation and Fusion are available in VMware's Public Beta Programs. The objective of VMware's Beta Programs is to gain customer feedback on these products. Public betas are available to anyone interested in testing new software and providing feedback to VMware's product & engineering teams.
VMware Labs is providing public access to the VMware Fusion Technology Preview 2012 to gather real-world feedback from users on a wide range of hardware and software configurations. The VMware Fusion Technology Preview includes changes to the core virtualization engine.
This Technology Preview includes changes to the underlying virtualization platform that are under active development. There are no guarantees that changes in this preview will be forward compatible with other VMware software, nor that these changes will be present in future supported releases of VMware Workstation. This Technology Preview does not include major new features.
- Installation and operation of VMware Workstation on Windows 8 and Windows Server 8
- Installation and operation of Windows 8 consumer preview and Windows Server 8 in a virtual machine
- Rendering and graphics correctness issues on all platforms and applications
- Linux 3D desktop experience, particularly when using the Ubuntu 12.04 LTS Beta
- Linux 3D application graphics correctness and performance
- Stability in real-world scenarios including suspend/resume and display and device support
- Nested Virtualization - running ESX and even trying Hyper-V* as a guest OS
- VNC connection performance and stability
VMware Labs is providing public access to the VMware Fusion Technology Preview 2012 to gather real-world feedback from users on a wide range of hardware and software configurations. The VMware Fusion Technology Preview includes changes to the core virtualization engine.
- Installation and operation of Windows 8 previews in a virtual machine
- Running Mac OS X (Mountain Lion) in a virtual machine
- Rendering and graphics correctness issues on all platforms and applications
- Linux 3D desktop experience, particularly Ubuntu 12.04 LTS and recent OpenSUSE releases, which should work out-of-the-box
- Linux 3D application graphics correctness and performance
- Changing boot devices in Mac OS X virtual machines
- Performance and stability of virtual machine power operations including suspend, resume, pause and restart
- Stability in real-world scenarios including suspend/resume and display and device plugging on the Mac
Saturday, March 10. 2012
Cool Tool - IgniteVM
IgniteVM is used by database administrators to ensure service and availability of database instances running in VMware virtual machines. It shows the DBA what the database response time delays are, and what the contributing causes are at the instance, virtual machine, and physical layers.
IgniteVM is a 24/7 monitoring tool, based on industry best practice Performance Intelligence and Wait-Time analysis methods. IgniteVM supports Oracle, SQL Server, DB2 LUW and Sybase databases across all operating systems, running in VMware vCenter Server or stand-alone ESX/ESXi host environments.
IgniteVM is a 24/7 monitoring tool, based on industry best practice Performance Intelligence and Wait-Time analysis methods. IgniteVM supports Oracle, SQL Server, DB2 LUW and Sybase databases across all operating systems, running in VMware vCenter Server or stand-alone ESX/ESXi host environments.
Wait-Time Analysis and Virtualization Visibility
Wait-time analysis is an approach to application and database performance improvement that allows users to see where users are waiting the most. Traditionally, database performance is measured in the number of events and hit ratios. While somewhat meaningful and easy to capture, these statistics do not reflect a relevant view of the end-user experience nor do they reveal with any precision where the problem originated.
IgniteVM gives DBAs visibility to see virtual server operation correlated with database instance wait-time analysis data. Assessing database performance without visibility leaves database administrators (DBAs) guessing about the root cause, hampering their ability to take action to address their most important user-oriented problems.
IgniteVM gives DBAs visibility to see virtual server operation correlated with database instance wait-time analysis data. Assessing database performance without visibility leaves database administrators (DBAs) guessing about the root cause, hampering their ability to take action to address their most important user-oriented problems.
Friday, March 9. 2012
Cool Tool - AlarmVM
AlarmVM is used by VMware Administrators to detect problems in the VMware environment and proactively notify administrators. alarmVM is a 24/7 alarm monitoring tool that detects problems in VMware objects, including VMs, hosts, clusters, datastores and vCenter Servers. When alarm conditions are detected, alarmVM notifies VMware Administrators via email and/or SNMP trap.
Key Benefits:
- alarmVM can be installed and set up to monitor a VMware environment in less than 20 minutes.
- It automatically activates out-of-the-box alarms so an entire VMware environment is being monitored simply by registering a vCenter Server.
- By default, alarmVM notifies all configured contacts about each alarm, eliminating the need to set up contacts for each alarm.
- Using inheritable alarm policies, it is easy to change default alarm behavior on entire sets of vSphere objects (e.g. all VMs in a datacenter or all VMs in a folder).
- A 30 day history of alarms is kept, so you can see what happened in the past. During this period, alarmVM shows graphs for metric-based alarms with the underlying detailed data that would not be available in vSphere Client.
- alarmVM shows how alarms are trending so you can see if trouble is easing or mounting in your VMware environment.
alarmVM consists of a multi-tiered architecture consisting of an alarmVM Server, Web Clients, a Repository database and Monitored vSphere Servers.
- alarmVM: The alarmVM Server performs two key functions. First, it collects data from the monitored VMware servers. Second, it presents web pages to alarmVM users and sends notifications (emails and SNMP traps) when alarm conditions are detected. It is installed on a server that has network access to the Repository and each of the monitored servers. Although this process performs many functions, it appears as a single process on the operating system.
- alarmVM Repository: The Repository database instance is accessed by the alarmVM Server, and holds all of the collected alarm information. A default Repository is installed with alarmVM, but alarmVM can be configured to use another database instance for the Repository.
- Monitored Servers: alarmVM’s agentless monitors remotely connect to each VMware vCenter Server or ESX/ESXi host and cause less than 1% overhead on the monitored systems. No software is installed in the vCenter Server, ESX/ESXi host or Virtual Machines. A vSphere user (aka monitoring user) with administrator privileges is needed for monitoring.
- Web Browsers: alarmVM users view alarm data in a web browser. From this interface, users register VMware servers, configure alarms and contacts for alarm notification.
Wednesday, March 7. 2012
New Book - Critical VMware Mistakes You Should Avoid
 There are thousands of How-to books on the market. This book is a hind-sight book. There are many common misconfigurations and mistakes that one can find over and over in virtual environments. This book is designed to illustrate some of these common mistakes and describe the impact on the virtual environment. In this book one can discover how/why these misconfigurations can cost your company piles of money, degrade performance and lower ROI for your virtual environment.
There are thousands of How-to books on the market. This book is a hind-sight book. There are many common misconfigurations and mistakes that one can find over and over in virtual environments. This book is designed to illustrate some of these common mistakes and describe the impact on the virtual environment. In this book one can discover how/why these misconfigurations can cost your company piles of money, degrade performance and lower ROI for your virtual environment.Of course after all of that, this book shows admins the proper way to configure the environment as well.
Topics include:
- Storage misconfigurations, impact, detection and best practices
- CPU misconfigurations, impact, detection and best practices
- Memory misconfigurations, impact, detection and best practices
- Network, impact, detection and best practices
- P2V migrations improper and proper methodologies
You've probably heard it said, Hindsight is 20/20. This book is hindsight taken from years of experience in the virtualization arena by the author. Grab all of the how-to books you like but make sure you pick up a copy of this book and avoid common pitfalls and mistakes of implementing a virtual environment.
Tuesday, March 6. 2012
We Have a Lift Off - CloudZoom - The Virtual Appliance Marketplace
![]() CloudZoom is a virtual appliance (cloud application) marketplace, providing users with a comprehensive catalog of all commercial and open source cloud apps for use in public, private, or hybrid cloud infrastructures. Cloud applications, also known as virtual appliances, are 'ready to run' software stacks (made of operating systems and applications) packaged as virtual images that can be deployed easily in cloud infrastructures. A few of the better known cloud application vendors are BitNami and JumpBox.
CloudZoom is a virtual appliance (cloud application) marketplace, providing users with a comprehensive catalog of all commercial and open source cloud apps for use in public, private, or hybrid cloud infrastructures. Cloud applications, also known as virtual appliances, are 'ready to run' software stacks (made of operating systems and applications) packaged as virtual images that can be deployed easily in cloud infrastructures. A few of the better known cloud application vendors are BitNami and JumpBox.
Sunday, March 4. 2012
Video - Build and Deploy Applications on Cloud Foundry
From this recorded webinar, you will to learn how to develop and deploy a simple application to the cloud in minutes.The first demo looks at how to deploy and scale a simple application to Cloud Foundry using multiple application services. The second demo shows you how to deploy a complex application on your laptop using Micro Cloud Foundry and scale to CloudFoundry.com without changing a single line of code.
Friday, March 2. 2012
Technical Paper - Cloud Infrastructure Architecture Case Study
The VMware Cloud Infrastructure Suite (CIS) consists of five technologies that together expand the capabilities and value that customers can realize from a virtualized infrastructure. CIS is designed to help organizations build more intelligent virtual infrastructures. It does so by enabling highly virtualized environments with the automation, self-service and security capabilities that customers require to deploy business-critical applications, respond to business demands more quickly and move to a secure cloud model. The CIS is based on the VMware vSphere platform as its foundation in pursuing any type of cloud infrastructure. In addition to vSphere, the CIS also includes VMware vShield App, VMware vCenter Site Recovery Manager Server (SRM Server), VMware vCloud Director, and VMware vCenter Operations Manager.
The VMware Cloud Infrastructure Architecture Case Study Series was developed to provide an understanding of the various components of the CIS. The goal is to explain how these components can be used in specific scenarios, which are based on real-world customer examples and therefore contain real-world requirements and constraints. This document is the first in a series of case studies, with each case study focusing on a different use case with different requirements and constraints.
This document provides both logical and physical design considerations encompassing components that are pertinent to this scenario. To facilitate the requirements of this case study, these considerations and decisions are based on a combination of VMware best practices and specific business requirements and goals. Cloud infrastructure–related components, including requirements and specifications for virtual machines and hosts, security, networking, storage, and management, are included in this document.
 Technical Paper - Cloud Infrastructure Architecture Case Study
Technical Paper - Cloud Infrastructure Architecture Case Study
The VMware Cloud Infrastructure Architecture Case Study Series was developed to provide an understanding of the various components of the CIS. The goal is to explain how these components can be used in specific scenarios, which are based on real-world customer examples and therefore contain real-world requirements and constraints. This document is the first in a series of case studies, with each case study focusing on a different use case with different requirements and constraints.
This document provides both logical and physical design considerations encompassing components that are pertinent to this scenario. To facilitate the requirements of this case study, these considerations and decisions are based on a combination of VMware best practices and specific business requirements and goals. Cloud infrastructure–related components, including requirements and specifications for virtual machines and hosts, security, networking, storage, and management, are included in this document.




